- Asa Vpn Load Balancing Configuration Sheet
- Asa Vpn Load Balancing Configuration Tool
- Cisco Vpn Load Balancing
- Asa Vpn Configuration
- Asa Vpn Load Balancing
- Cisco Asa Vpn Configuration Guide
8
Load Balancing IPSEC Traffic
Many customers are dealing with COVID-19 and need a quick solution to allow their employees to work from home securely. Cisco has put together packages to he. Internet Load Balancing and Failover for Multiple ISP Links. Controlling traffic is a key facet of internet management. Sometimes primary connections will go down. Or too much traffic may cause congested links or overwhelmed devices to become unusable. We wrote about the implementation of load balancing in the cloud in a 2017 blog post.
Configuring load balancing IPSEC traffic across VPN gateways
The previous chapter shows how to load balance across three VPN gateways. The IPSEC protocol (Internet Protocol Security) enables you to load balance between gateways as well. Figure 8.1 shows inbound IPSEC traffic being load balanced to one of three destination VPN gateways.
Figure 8.1 VPN load balancing between VPN gateways
In this configuration, address translation is on, and IPSEC is in tunnel mode with ESP (Encapsulation Security Payload) specified. The hop shown by the blue arrow represents the IPSEC part of the transmission. A packet originating from Client1 with Client6 as its destination is encapsulated by the VPN gateway (VPN5) serving the client and traverses the Internet in this secure form. The BIG-IP then load balances the packet to one of three destination gateways: VPN1, VPN2, or VPN3. The VPN to which it is load balanced then becomes the established gateway, or tunnel, for packets from VPN5. Traffic from Client1, a separate VPNconnection, would be load balanced to a different destination VPN.
For this configuration to work, IPSEC requires certain special settings on the clients and servers, and on the BIG-IP:
- On clients and servers, IPSEC must be configured in tunnel mode with ESP.
- You must enable Any IP mode for the virtual servers on the BIG-IP.
- Enable address translation on the BIG-IP.
- Enable UDP on the BIG-IP to support internet key exchange (IKE) traffic.
- Enable persistence across services on the BIG-IP.
Configuring IPSEC load balancing
First, configure your servers and clients for IPSEC tunnel mode with ESP. Refer to the documentation provided with the server or client. Be sure to use the same security association for all clients.
Next, complete the following tasks on the BIG-IP:
- Create two load balancing pools
Create two load balancing pools for the VPN destination gateways, one specifying port 500 for internet key exchange, one specifying a wildcard service (0) forAny IP mode. - Create two virtual servers
Create two virtual servers for referencing the two pools, one specifying port 500 for internet key exchange, one specifying a wildcard service (0) for Any IP (IPSEC) traffic. - Enable UDP
Enable UDP for internet key exchange (IKE) traffic. - Enable persistence
Enable persistence across services.
Defining the pools
To configure IPSEC load balancing, you first define one pool that load balances the VPN destination gateways with a wildcard port, and one pool that load balances the VPN destination gateways handling service 500 traffic.
To create the pools using the Configuration utility
- In the navigation pane, click Pools.
The Pools screen opens. - Click the Add button.
The Add Pool screen opens. - For each pool, enter the pool name and member addresses in the Add Pool screen. (For additional information about configuring a pool, click the Help button.)
Configuration notes
Create a VPN pool named vpn_anyip. This pool contains the outside addresses of the three VPN destination gateways with service zero.
Create a VPN pool named vpn_ike. This pool contains the outside addresses of the three VPN destination gateways with service 500.
To define pools from the command line
Use the following syntax to define the pools at the command line:
b pool <pool_name> { member <member1> member < member2> ...> }
To create the configuration described in this solution, type the following commands:
member 10.1.10.1:0
member 10.1.10.2:0
member 10.1.10.3:0 }
b pool vpn_ike {
member 10.1.10.1:500
member 10.1.10.2:500
member 10.1.10.3:500 }
Defining the virtual servers
After you define the pools for the VPNs, you can define the following virtual servers, one to load balance Any IP (IPSEC) traffic, and one to load balance internet key exchange traffic.
To define the virtual server using the Configuration utility
Asa Vpn Load Balancing Configuration Sheet
Use this procedure for each BIG-IP that you need to configure.
- In the navigation pane, click Virtual Servers.
- Click the Add button.
The Add Virtual Server screen opens. - For each virtual server, enter the virtual server address and pool name. (For additional information about configuring a virtual server, click the Help button.)
- Fill in the attributes for the virtual server. For additional information about this screen, click the Help button.
- For each of the two VPN load-balancing virtual servers:
- Click the Virtual Address Properties tab.
The Virtual Address Properties screen opens. - In the Any IP Traffic field, check the Enable box. Then click Apply.
Configuration notes
Create the virtual server 192.168.13.100:0 and use the pool vpn_anyip.
Create the virtual server 192.168.13.100:500 and use the pool vpn_ike.
To define the virtual servers from the command line
Define the virtual servers from the command line as follows:
b virtual 192.168.13.100:0 use pool vpn_anyip
b virtual 192.168.13.100:500 use pool vpn_ike
Then, enable Any IP for both virtual servers:
b virtual 192.168.13.100 any_ip enable.
Enabling UDP
After you enable the Any IP feature for the virtual servers, enable UDP 500 so the BIG-IP can handle internet key exchange (IKE) traffic:
b service 500 udp enable
Enabling persistence across services
Finally, complete the configuration by setting up persistence across services on the BIG-IP:
b global persist_across_services enable
IPSEC VPN sandwich configuration
You can load balance content servers to incoming IPSEC traffic by adding a second BIG-IP in a VPN sandwich configuration. Figure 8.2 shows the VPN sandwich configuration.
Figure 8.2 VPN load balancing between VPN gateways
When you set up the sandwich configuration, the configuration tasks you use are identical to those you use for the basic VPN IPSEC configuration. The exceptions are that you configure a load balancing pool and virtual server on the second BIG-IP. For example:
- Create a VPN pool named server_pool. This pool contains as members the addresses of the four content servers, server1, server2, server3, and server4.
- Create the virtual server 10.1.20.10:80 and use the pool server_pool.
Defining the additional pool
Asa Vpn Load Balancing Configuration Tool
To create the pool using the Configuration utility
For the BIG-IP in Figure 8.2 labeled BIG-IP 2:
- In the navigation pane, click Pools.
The Pools screen opens. - Click the Add button.
The Add Pool screen opens. - For each pool, enter the pool name and member addresses in the Add Pool screen. (For additional information about configuring a pool, click the Help button.)
Configuration note
Create a VPN pool named server_pool. This pool contains as members the addresses of the four content servers, server1, server2, server3, and server4.
To define the pool from the command line
Use the following syntax to define the pools from the command line:
b pool <pool_name> { member <member1> member < member2> ...> }
To create the configuration described in this solution, type the following command.
b pool server_pool {
member 10.1.20.1:80
member 10.1.20.2:80
member 10.1.20.3:80
member 10.1.20.4:80 }
Defining the additional virtual server
To define the additional virtual server using the Configuration utility
For each BIG-IP to be configured:
- In the navigation pane, click Virtual Servers.
The Virtual Servers screen opens. - Click the Add button.
The Add Virtual Server screen opens. - For each virtual server, enter the virtual server address and pool name. (For additional information about configuring a virtual server, click the Help button.)
To define the virtual server from the command line
To define the virtual server from the command line, type the following command.
b virtual 10.1.20.10:80 use pool server_pool
Additional configuration options
Whenever a BIG-IP is configured, you have a number of options:
- You have the option in all configurations to configure a BIG-IP redundantsystemfor fail-over. Refer to Chapter 5, Configuring a Redundant System, in the BIG-IP Reference Guide.
- All configurations have health monitoringoptions. Refer to Health Monitors in Chapter 3, Configuring the High-Level Network, in the BIG-IP Reference Guide.
- When you create a pool, there is an option to set up persistence and a choice of load balancing methods. Refer to Pools in the Chapter 3, Configuring the High-Level Network, in theBIG-IP Reference Guide.
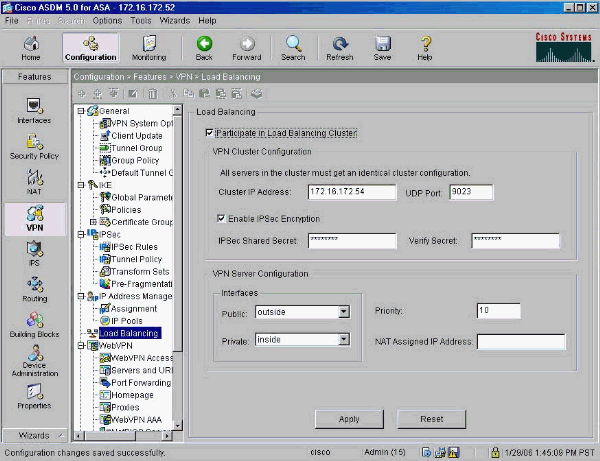
Reference: Cisco ASA Series VPN ASDM Configuration Guide – Updated 31/3/2014
Load Balancing Licensing Requirements:
- To use VPN load balancing, you must have an ASA Model 5510 with a Plus license or an ASA Model 5520 or higher.
- VPN load balancing also requires an active 3DES/AES license – The security appliance checks for the existence of this crypto license before enabling load balancing.
Load Balancing Prerequisites:
- You must have first configured the ASA’s public and private interfaces before configuring load balancing.
- You must have previously configured the interface to which the virtual cluster IP address refers.
- All devices that participate in a cluster must share the same cluster-specific values: IP address, encryption settings, encryption key, and port
- All of the outside and inside network interfaces on the load-balancing devices in a cluster must be on the same IP network.
- If you have a remote-client configuration in which you are using two or more ASAs connected to the same network to handle remote sessions, you can configure these devices to share their session load
- Load balancing directs session traffic to the least loaded device, thus distributing the load among all devices.
- Creating Virtual Clusters
- Geographical Load Balancing
- Comparing Load Balancing to Failover
- Load Balancing Licensing Requirements
- Load Balancing Prerequisites
- Eligible Clients
- Configuring Load Balancing (Without the Wizard)
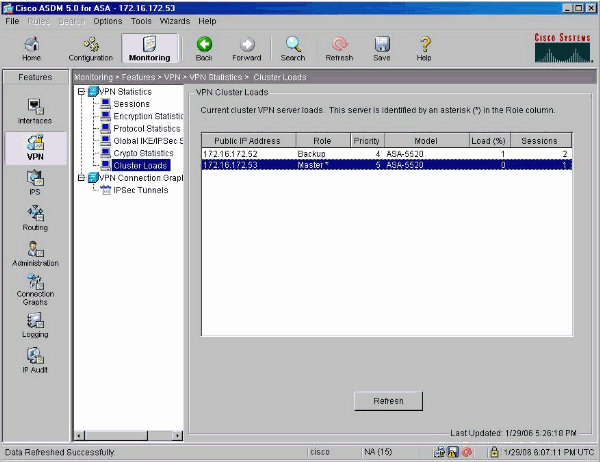
All devices in the virtual cluster carry session load.
One device in the virtual cluster, the virtual cluster master, directs incoming connection requests to the other devices, called backup devices.
- keeps track of how busy each is,
- and distributes the session load accordingly.
The role of virtual cluster master is not tied to a physical device. – One of the backup devices in the cluster takes over that role.
The virtual cluster appears to outside clients as a single virtual cluster IP address. This IP address is not tied to a specific physical device.
A VPN client attempting to establish a connection connects first to this virtual cluster IP address.
The virtual cluster master then sends back to the client the public IP address of the least-loaded available host in the cluster.
- In a second transact ion (transparent to the user) the client connects directly to that host.
Geographical load balancing for VPN often uses a Cisco Global Site Selector (GSS)
- The GSS uses DNS for the load balancing, and the time to live (TTL) value for DNS resolution is defaulted to 20 seconds.
- Increasing to a much higher value allows ample time for the authentication phase when the user is entering credentials and establishing the tunnel.
#Configuring the Public and Private Interfaces for Load Balancing
!
interface GigabitEthernet0
nameif outside
security-level 0
ip address 10.10.10.1 255.255.255.0
!
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.16.1 255.255.255.0
!
ASA-1(config)# vpn load-balancing
ASA-1(config-load-balancing)# interface lbpublic outside >Configure the public interface
ASA-1(config-load-balancing)# interface lbprivate inside >Configure the private interface
ASA-1(config-load-balancing)# priority 8 >(1-10) Higher is more likely to become the virtual cluster master
!
#Configuring the Load Balancing Cluster Attributes
!
ASA-2(config-load-balancing)# cluster ip address 10.10.10.10
ASA-2(config-load-balancing)# cluster port 9023
#################################################
# Optional
#################################################
Cisco Vpn Load Balancing
ASA-2(config-load-balancing)# cluster key Cisco123
Asa Vpn Configuration
ASA-2(config-load-balancing)# cluster encryption
#################################################
Asa Vpn Load Balancing
ASA-2(config-load-balancing)# participate
#Configuring the Load Balancing Cluster Attributes
Cisco Asa Vpn Configuration Guide
ASA-1(config-load-balancing)# sh vpn load-balancing
